Find more at Tech Savvy Youth's Blog. The following article is a TSY Blog post regarding the technology of Encryption.
As our world becomes increasingly digital, the need for cybersecurity and protection has grown. Encryption is a fundamental part of modern cybersecurity that helps protect our data from unauthorized access or interception. Cryptography is the study of techniques used to secure communication. Encryption enables us to safeguard our financial information, personal conversations, and passwords. For instance, web browsers often ask us if we want to save our passwords for future use, and these passwords are encrypted to ensure their safety.
But what does that mean??
To put it simply, encryption is the process of converting data into an encoded form that is different from the original data. This encoded data is then transmitted or stored where it cannot be deciphered by anyone who comes across it. Decryption is the process of using algorithms that correspond with encryption to reverse it and obtain the original data. It's like playing a secret language game where only you and your friends know the meaning. An encryptor is an algorithm or device that converts information into 'ciphertext', which is the encrypted format of the data. A decryptor is another algorithm that can reverse encryption by interpreting the ciphertext and producing the original data in a readable format.
How did it originate?
The origins of encryption can be traced back to as early as 1900BC in both Egyptian and European history. While cryptography was present in ancient civilizations, it became a valuable tool during the formation of many empires. The competition and conflicts among these empires led to concerns about the security of messengers carrying letters with sensitive information. Military strategies, messages from monarchs, and secret espionage details were shared through encrypted handwritten letters that could only be decoded by those who possessed the key. The modern principles of cryptography were developed during World War II. The most famous exapmle is the German enigma machine which marked the beginning of the use of mechanical devices for encoding data. The enigma was used to encrypt data about tactical military movements, surprise attacks, and intelligence information.
A contemporary exapmple:
Consider the use of encryption in texting. When you write a message to your friend, you use language that is easily understandable to both of you. However, if the texting service uses encryption, your message is transformed into ciphertext, using the encryption algorithm utilized by the service provider. This ciphertext is then sent over the internet to your friend. Upon arrival, the decryptor algorithm is used to convert the ciphertext back into the original message you had written, making it comprehensible to your friend.
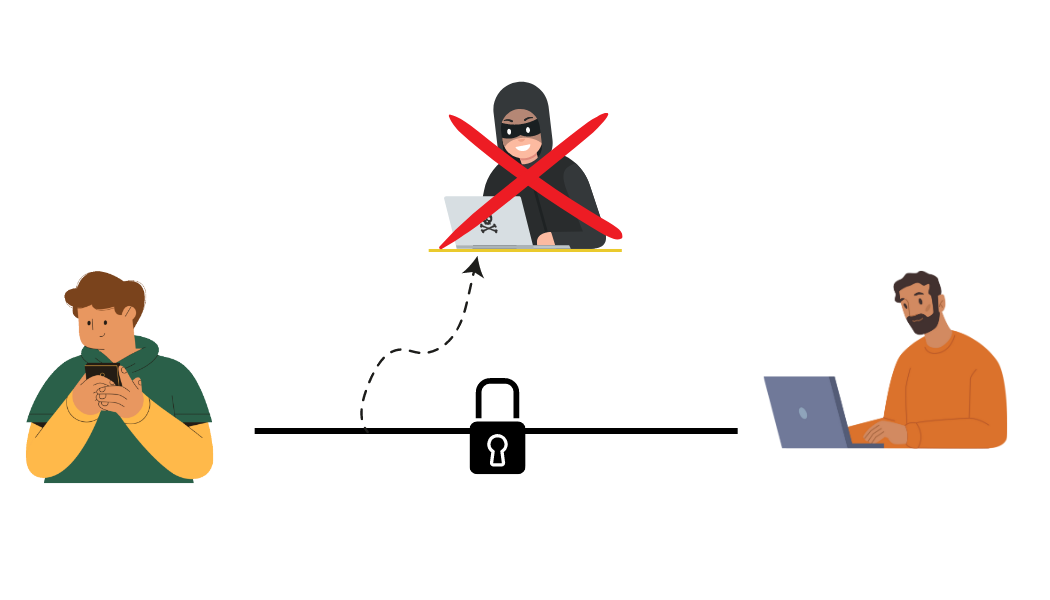
How does encryption ensure the security of our data?
When sensitive information is transmited over the internet, encryption algorithms scramble the data into an ciphertext. Even if a hacker intercepts the data during transmission, they will only be able to access the ciphertext, which is meaningless without the decryption key. Encryption protects our data from cyber threats such as hacking, interception, and data breaches, and prevents unauthorized tampering or editing of our information. Thus, encryption is a critical component of modern cybersecurity that helps safeguard our sensitive information.
Who uses encryption??
Encryption is widely used among information technology companies, financial institutions, banking firms, government, military, communication systems, etc. Encryption is the base of modern communication and safety. Unknowingly, everyone uses encryption through the services and facilities they use every day. Texting and social media softwares use encryption to transmit messages and data over the internet, corporate firms use encryption to store their sensitive information. Governments use encryption to safeguard information regarding national security. Armed forces use encrypted codes and passcodes for their operations. Important details and strategies are communicated through encryption.
Signing Off,
Atharva Saraf